Announcing free cybersecurity and consulting services. Read announcement
Bespoke cyber defense for governments, global enterprises, and innovators operating in hostile digital environments. From custom-built secure systems to AI modules that integrate seamlessly into existing networks, our solutions monitor, predict, and neutralize threats in real time.
We don’t just secure systems — We secure legacies.
Intelligence.
InfiniteIntegrations.
From legacy systems to cutting-edge stacks, our technology unifies and enhances security across your entire ecosystem.
Empowering enterprises with AI-driven cybersecurity, precision-engineered software, and expert insight — safeguarding your digital future while accelerating innovation.
Precision.
ZeroCompromise.
In today’s threat landscape, milliseconds matter. Our AI-Powered Cybersecurity platform is more than just protection — it’s an autonomous security ecosystem engineered to outpace attackers.
By unifying XDR and SIEM into a single AI-driven framework, it delivers continuous real-time monitoring, instant breach alerts, and autonomous remediation across endpoints, workloads, and cloud environments. Every action is orchestrated by AI, giving your business a living, adaptive defense system that never sleeps.
Imagine a live security dashboard that gives you:
✅ Full visibility across your IT infrastructure in real-time
✅ AI-driven threat intelligence that evolves as fast as attackers do
✅ Instant remediation on endpoints before threats spread
✅ Granular compliance and vulnerability insights at your fingertips
🔒 Our system doesn’t just react — it predicts. Leveraging advanced machine learning, it analyzes billions of signals across your network to anticipate threats before they emerge, ensuring your business remains secure, resilient, and always a step ahead.
Your enterprise deserves more than reaction — it deserves anticipation. With our system, you’re not just protected, you’re untouchable. This is intelligence at the edge, vigilance at the core, and resilience at scale.
Imagination
Ends, OurEngineering
Begins.In a world where technology defines competitive edge, your ideas deserve more than off-the-shelf solutions — they deserve limitless creation. Our Custom AI-Enhanced Software service is not just development, it’s digital craftsmanship powered by intelligence and precision.
From lightweight web pages that load at lightning speed, to enterprise-scale ecosystems that empower thousands of users, from autonomous AI models that learn and adapt, to advanced cybersecurity research tools including controlled malware and virus simulators for red-teaming — our engineers build with no boundaries. Every project is approached as a living, evolving system designed to scale and transform with your vision.
✨ Imagine software that:
✅ Automates and optimizes workflows, turning hours of work into seconds
✅ Seamlessly integrates AI into your everyday operations and decision-making
✅ Evolves continuously with predictive intelligence — never becoming obsolete
✅ Translates even the boldest, most futuristic ideas into working reality
✅ Bridges creativity and engineering to deliver experiences that feel alive
🔮 This isn’t just development — it’s creation without limits. By fusing cutting-edge AI with deep engineering expertise, we ensure that every build is smarter, faster, and more adaptive than traditional solutions.
Vision,
OurGuidance
— Limitless, Precise, andFree.
In a digital era where every decision shapes resilience and growth, the right strategy is more valuable than any tool. Our Strategic Tech & Security Consultation service gives you unrestricted access to expert minds — without the barrier of cost.
Whether you’re navigating the complexities of cyber defense, planning the architecture of a next-generation enterprise platform, exploring the use of AI in business, or simply validating your ideas against industry standards, we provide tailored insights that are clear, actionable, and forward-looking.
⚡ Imagine having access to:
✅ Elite-level cybersecurity and technology experts advising you without hidden fees
✅ Clarity in chaos — making sense of complex technical landscapes
✅ Custom roadmaps for scaling your business securely and intelligently
✅ A sparring partner for innovation — refining even your wildest ideas into achievable strategies
✅ Unbiased, vendor-agnostic advice focused only on your success
🧭 Consultation isn’t a transaction — it’s partnership. We stand beside you as strategists, innovators, and defenders, ensuring every choice you make is fortified by knowledge and foresight.
Enemy.
Defend Like AWarrior.
Cyber defense isn’t enough when adversaries are relentless. To be truly secure, you must become the attacker before they do. Our Offensive Security & Red-Teaming service goes beyond traditional testing — it’s a full-scale simulation of real-world threats, designed to expose cracks in your defenses before attackers exploit them.
We don’t just scan. We hunt. We don’t just test. We break. And then we show you how to build back stronger.
💀 With this service, you gain:
✅ Advanced penetration testing across networks, applications, and cloud infrastructure
✅ Red-team operations that mirror state-sponsored, zero-day-level attacks
✅ Physical & social engineering assessments to test the human layer of your defense
✅ Detailed exploit chains showing exactly how attackers could move through your systems
✅ Actionable, prioritized remediation plans to close every gap before it’s too late
⚔️ Our approach is adversarial by design, but constructive in purpose. Every engagement is executed by elite cybersecurity operators who specialize in thinking like attackers but acting as your defenders.
Currency.
We Make ItInvincible.
In today’s economy, data isn’t just information — it’s power. But power without protection is vulnerability. Our Secure Data Brokerage service ensures your most sensitive assets are exchanged, transferred, and stored with absolute confidentiality, integrity, and control.
We don’t just protect your data — we fortify it into an unbreakable asset. We don’t just move information — we move trust across every transaction.
💠 With this service, you gain: ✅ End-to-end encrypted data exchange for individuals, enterprises, and government use
✅ Zero-Trust enforcement on every transfer, ensuring only the right entities gain access
✅ Blockchain-backed audit trails for unalterable proof of every transaction
✅ AI-driven anomaly detection to prevent tampering or unauthorized access in real time
✅ Granular access control policies that let you define exactly who sees what
🔐 Whether it’s intellectual property, classified government intelligence, or corporate trade secrets — our system ensures your data remains untouchable, untraceable, and uncompromised.
This is not just secure storage.
This is data sovereignty as a service — power, privacy, and protection engineered at scale.
Comprehensive Cyber Defense that Monitors, Detects, and Neutralizes Risks Across Systems, Networks, and Applications Before They Can Escalate. Designed for Enterprises That Demand Zero Weak Points.
Defend against today’s most advanced cyberattacks with AI-driven Extended Detection and Response (XDR). Our platform continuously identifies, analyzes, and neutralizes threats across endpoints, networks, and cloud workloads — ensuring rapid containment before damage is done.
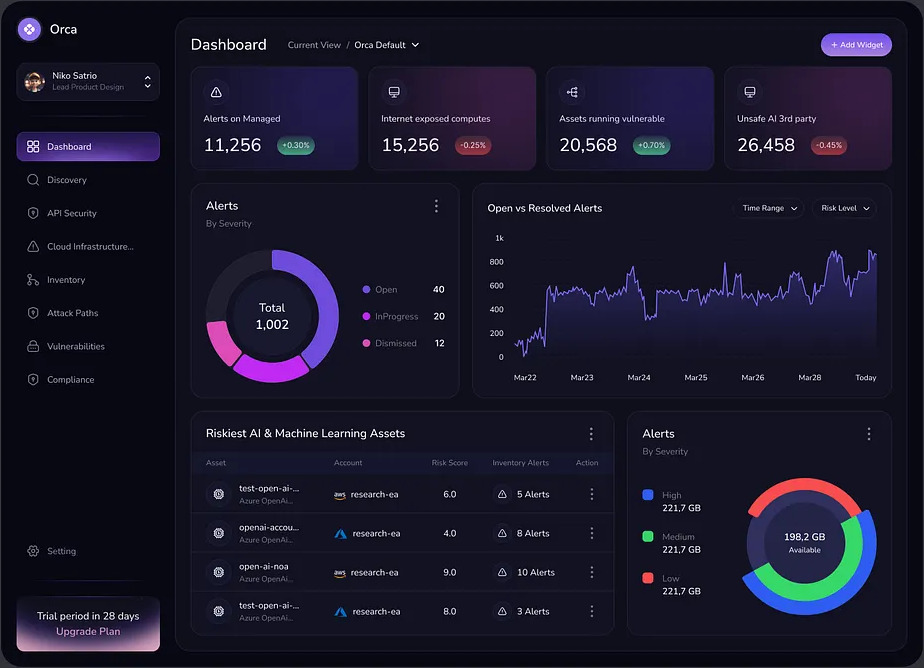
Stay ahead with continuous visibility into every layer of your IT environment. From endpoint activity to cloud traffic, our real-time monitoring and live dashboards provide instant alerts, enabling proactive defense before incidents escalate.
Gain complete control over your security posture with an intelligent Security Information and Event Management (SIEM) solution. By correlating logs, detecting anomalies, and automating responses, we empower your team to make informed decisions faster.

Potential
ofYggdrasil Security.
The Yggdrasil Cloud service offers managed, ready-to-use, and highly scalable cloud environments for security monitoring and endpoint protection.
Enable your workforce to connect from anywhere without exposing your infrastructure. Our platform enforces continuous verification, encrypted tunnels, and AI-driven risk assessments — ensuring every login, device, and session is trusted, monitored, and protected.
Join
ourOpen Source Community.
Connect with industry experts and access free support tailored to your needs. Gain consulting insights to strengthen your digital systems and strategies. Be part of a trusted network shaping the future of secure technology.
Your most important questions, answered. Learn how Yggdrasil empowers businesses with next-generation cybersecurity, AI-driven solutions, and strategic consulting.
What services does Yggdrasil provide?
How does Yggdrasil ensure data security for clients?
Do you offer consulting services for enterprises?
Can Yggdrasil build custom solutions for my business?
What industries does Yggdrasil work with?
How does Yggdrasil’s AI Cybersecurity protect businesses?
Updated
withCyber Insights.
Subscribe to our newsletter and get the latest app updates, exclusive cybersecurity insights, and industry news delivered directly to your inbox.